Rule Severity
Overview
Rule severities are used to help you prioritize alerts during the triage or investigation process.
You can think of severity as confidence-weighted impact, where confidence is how likely an alert is a true positive, and impact is the damage the attack the rule is designed to detect could cause.
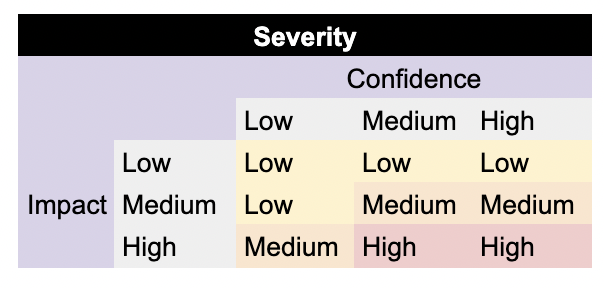
Severities
criticalis used to identify rules related to CVEs, malware families, and threat actors.criticalalerts that were not auto-remediated should be reviewed immediately.criticalcan also be used for high-confidence, high-impact alerts that you want prioritized over everything else that ishigh.highalerts that were not auto-remediated should be reviewed quickly.mediumalerts that were not auto-remediated should be reviewed frequently.lowalerts that were not auto-remediated should be reviewed regularly.
A given rule's severity may not be appropriate for everyone because organizations have different compensating controls. For example, a Microsoft 365 credential phishing attack may have a lower severity for organizations enforcing hardware-based MFA. The rules in the Sublime Rules Feed assume minimal compensating controls.
Updated 4 months ago