Role-Based Access Control (RBAC)
Sublime's built-in and custom roles make it easy to give your team the perfect amount of access.
Managing Roles
When you create a new user from the Admin > Account page, you'll have the option to select a role.
To change an existing user's role, select the user in the Users table, select Actions > Edit, and update the user's role.
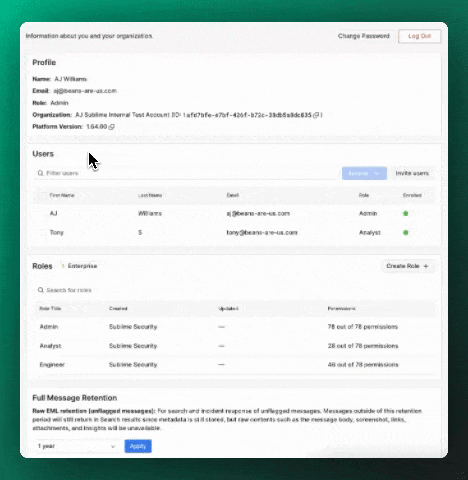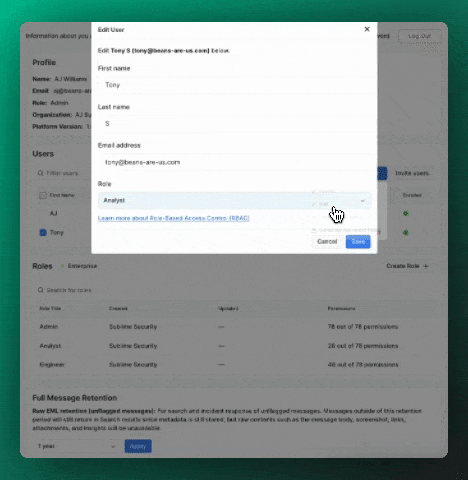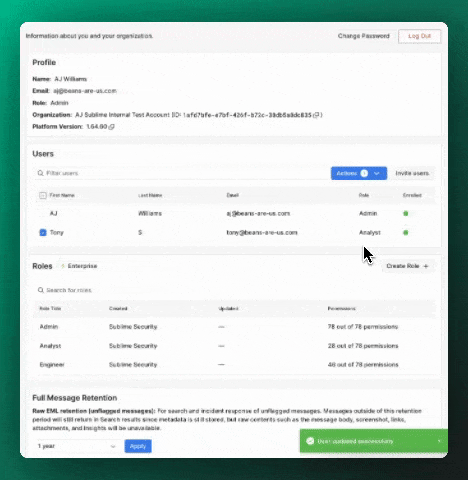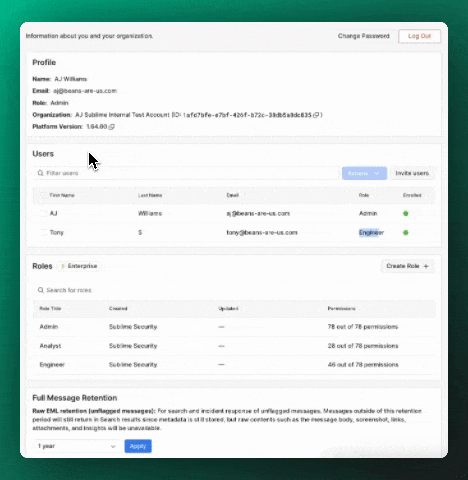
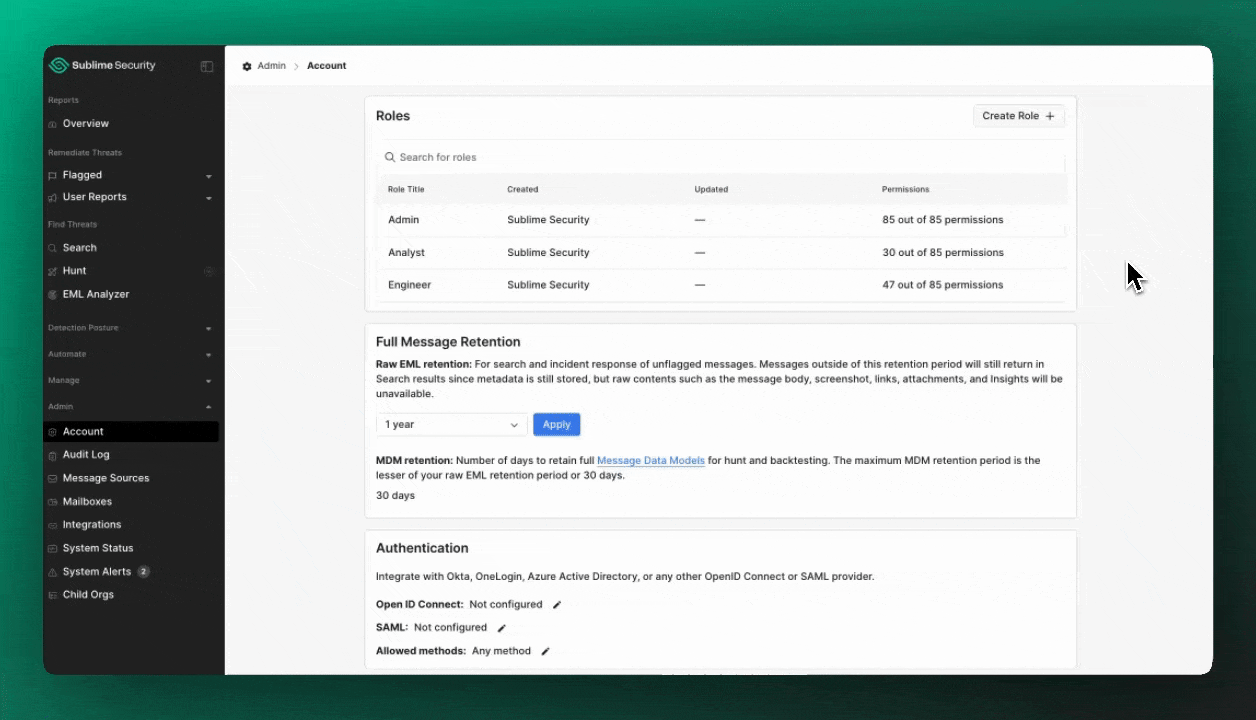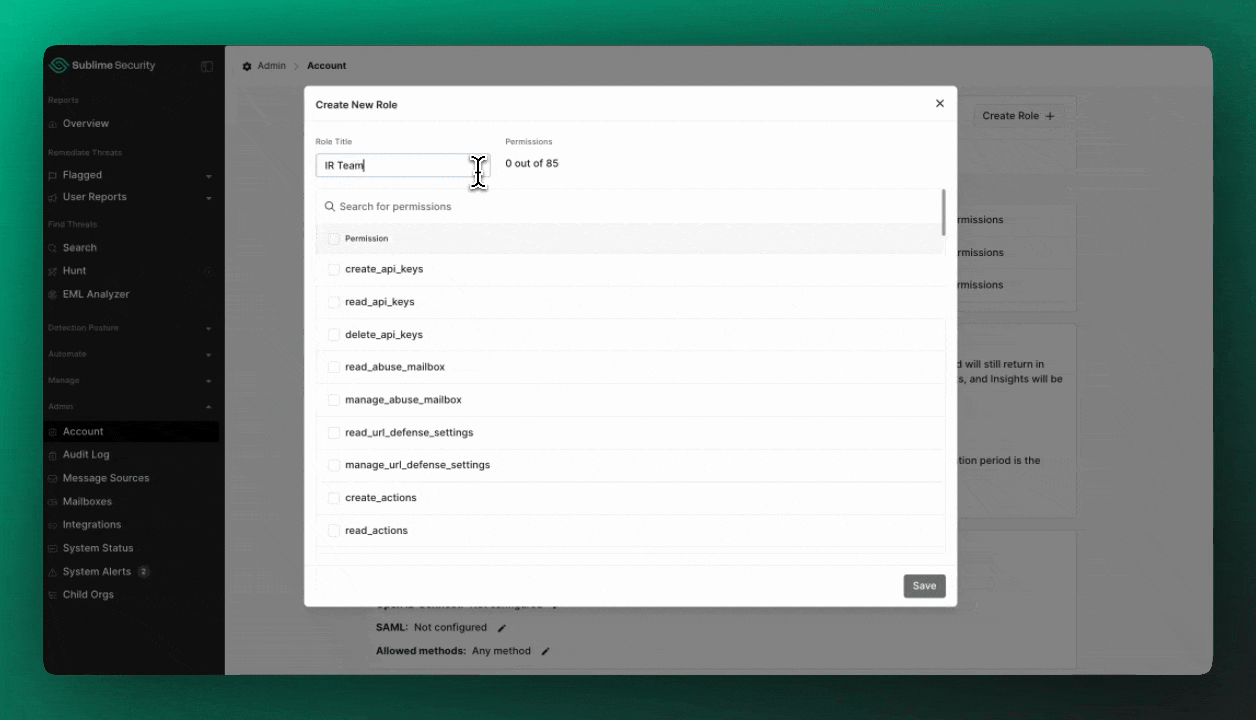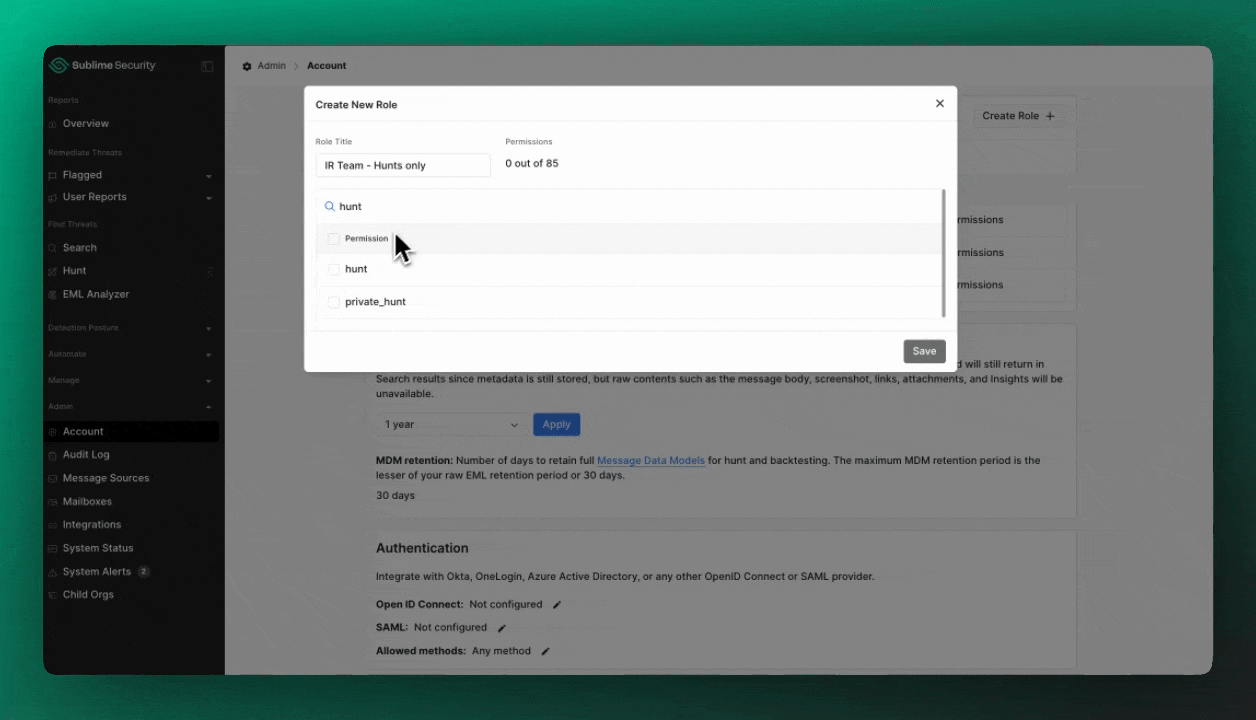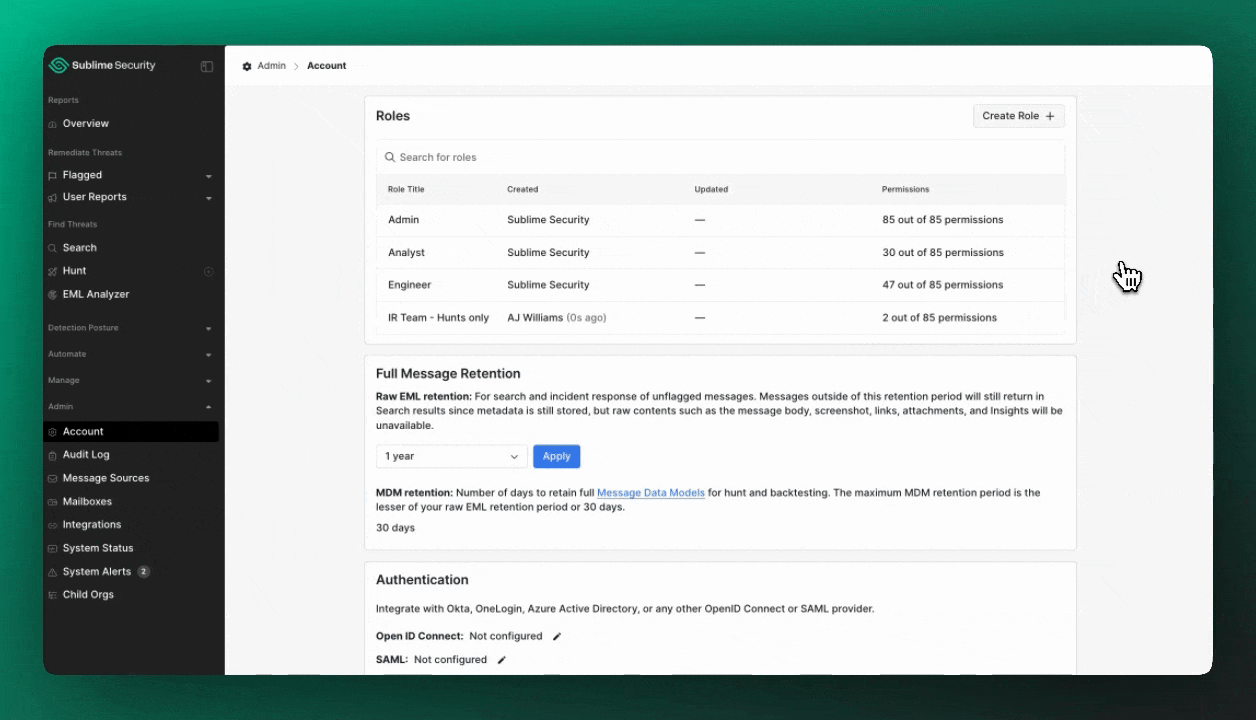
Roles
| Role | Description |
|---|---|
Admin | All Sublime features, including the ability to create custom roles. |
Engineer | Build detection rules, Backtest, Hunt, investigate and remediate flagged and user reported messages, view system error notifications, and more. |
Analyst | Investigate and remediate flagged and user reported messages, view system error notifications. Cannot create or modify rules, Search, Backtest, or Hunt. |
Custom | Anyone with the Admin role can create a custom role with granular permissions. |
The below table enumerates the Sublime Platform permissions and denotes which role contains it. A green check ✅ denotes that the permission is included in the role. A green check with an asterisk ✅* denotes that the role has the listed permission, but can only operate on resources that the current user has created themselves (e.g. an Engineer can only read API keys that were created by themselves, whereas an Admin can read API keys regardless of which user they were created by).
| Category | Permission | Admin | Engineer | Analyst |
|---|---|---|---|---|
| Audit Log | manage_audit_log | ✅ | ||
| Audit Log | read_audit_log | ✅ | ||
| IP Allowlist | manage_ip_allowlist | ✅ | ||
| IP Allowlist | read_ip_allowlist | ✅ | ✅ | ✅ |
| MDM Retention | update_full_message_retention | ✅ | ||
| Mailbox Auto-Activation | read_auto_activate | ✅ | ✅ | ✅ |
| Mailbox Auto-Activation | update_auto_activate | ✅ | ||
| Abuse Mailbox Settings | manage_abuse_mailbox | ✅ | ✅ | |
| Abuse Mailbox Settings | read_abuse_mailbox | ✅ | ✅ | ✅ |
| API Keys | create_api_keys | ✅ | ✅* | ✅* |
| API Keys | read_api_keys | ✅ | ✅* | ✅* |
| API Keys | delete_api_keys | ✅ | ✅* | ✅* |
| API Keys | set_external_api_keys | ✅ | ✅* | |
| API Keys | read_external_api_keys | ✅ | ✅* | |
| Users | create_users | ✅ | ||
| Users | read_users | ✅ | ✅ | ✅ |
| Users | update_users | ✅ | ||
| Users | delete_users | ✅ | ||
| Users | invite_users | ✅ | ||
| Message Sources | create_message_sources | ✅ | ||
| Message Sources | read_message_sources | ✅ | ✅ | ✅ |
| Message Sources | read_message_sources_inline_message_meta | ✅ | ||
| Message Sources | update_message_sources | ✅ | ||
| Message Sources | delete_message_sources | ✅ | ||
| Mailboxes | read_mailboxes | ✅ | ✅ | ✅ |
| Mailboxes | activate_mailbox | ✅ | ||
| Mailboxes | deactivate_mailbox | ✅ | ||
| Rules | create_rules | ✅ | ✅ | |
| Rules | read_rules | ✅ | ✅ | ✅ |
| Rules | update_rules | ✅ | ✅ | |
| Rules | delete_rules | ✅ | ✅ | |
| Lists | create_lists | ✅ | ✅ | |
| Lists | read_lists | ✅ | ✅ | ✅ |
| Lists | update_lists | ✅ | ✅ | ✅ |
| Lists | delete_lists | ✅ | ✅ | |
| Actions | create_actions | ✅ | ✅ | |
| Actions | read_actions | ✅ | ✅ | ✅ |
| Actions | update_actions | ✅ | ✅ | |
| Actions | delete_actions | ✅ | ✅ | |
| Actions | associate_rules_to_actions | ✅ | ✅ | |
| Feeds | create_feeds | ✅ | ✅ | |
| Feeds | read_feeds | ✅ | ✅ | ✅ |
| Feeds | update_feeds | ✅ | ✅ | |
| Feeds | delete_feeds | ✅ | ✅ | |
| Backtest | backtest | ✅ | ✅ | |
| Hunt | hunt | ✅ | ✅ | |
| Hunt | private_hunt | ✅ | ||
| Search | search | ✅ | ✅ | |
| Investigation | access_all_message_contents | ✅ | ✅ | ✅ |
| Investigation | access_flagged_message_contents | ✅ | ✅ | ✅ |
| Investigation | access_user_reported_message_contents | ✅ | ✅ | ✅ |
| Remediation | perform_actions | ✅ | ✅ | ✅ |
| Error Log | access_error_logs | ✅ | ✅ | ✅ |
| URL Defense | read_url_defense_settings | ✅ | ||
| URL Defense | manage_url_defense_settings | ✅ | ||
| Content viewing setting | manage_view_contents_requirements | ✅ | ||
| OIDC setting | manage_oidc | ✅ | ||
| OIDC setting | read_oidc | ✅ | ✅ | ✅ |
| SCIM | read_scim_resources | ✅ | ✅ | ✅ |
| Provider group | read_provider_groups | ✅ | ✅ | ✅ |
| Provider group | update_provider_groups | ✅ | ✅ | ✅ |
| Exclusions | create_exclusions | ✅ | ||
| Exclusions | read_exclusions | ✅ | ✅ | ✅ |
| Exclusions | update_exclusions | ✅ | ||
| Exclusions | delete_exclusions | ✅ | ||
| Historical ingestion | start_historical_ingestion_jobs | ✅ | ||
| Historical ingestion | abandon_historical_ingestion_jobs | ✅ | ||
| Historical ingestion | read_historical_ingestion_jobs | ✅ | ✅ | ✅ |
| Roles | read_roles | ✅ | ✅ | ✅ |
| Roles | set_delegated_user_default_role | ✅ | ||
| Roles | can_access_child_orgs | ✅ | ||
| Telemetry | manage_telemetry | ✅ | ||
| Deletion | delete_org | ✅ | ||
| Polling setting | manage_message_polling | ✅ | ||
| Overview Report | read_org_stats | ✅ | ✅ | ✅ |
| Overview Report | read_remediation_stats | ✅ | ✅ | ✅ |
| Link clicks | read_link_clicks | ✅ | ||
| S3 export | manage_message_export | ✅ | ||
| Setup guide | manage_account_setup_guide | ✅ | ||
| Message creation | create_new_message | ✅ | ✅ | ✅ |
API Key PermissionsAPI keys reflect the RBAC permissions of the creating user at the time the key was generated.
Custom roles
You can create an unlimited number of custom roles within your organization by heading to Admin > Account and clicking Create Role.
Multi-tenant custom roles
For multi-tenant instances, custom roles can only be created or managed by the parent org. While Admins can assign custom roles to team members on any child org, they can't create new roles or edit the permissions on existing roles via the child org.
Team members who have access to the parent org will inherit their existing role when they log into the child org for the first time. Admins can change their role afterwards if they want that team member to have a different role on a specific child org.
All custom roles created by the parent org are available to all of the child orgs, so we recommend that custom role names don't include child org information, such as business names. You can alternatively limit anyone with a custom role from seeing available roles by withholding the read_roles permission.
Additionally, multi-tenant environments include permissions that control user propagation and cross-org access. The set_delegated_user_default_role permission defines the default role assigned when users are automatically propagated to child orgs, while can_access_child_orgs controls whether a user can access child and descendant orgs. Users without the can_access_child_orgs permission will still appear in child orgs but will be shown in a disabled state indicating they cannot access the org.
Updated 3 days ago