ASA: Autonomous Security Analyst
Overview
The Autonomous Security Analyst (ASA) is an AI analyst that inspects user-reported and suspicious flagged messages, provides detailed analysis, and triages the messages to help security teams overcome any volume of user-reported messages or grey-area flagged messages.
ASA addresses key pain points for security teams:
- Security analysts overwhelmed by high volumes of user-reported messages or gray-area flagged messages can reduce the number of manual reviews required with ASA’s automated analysis.
- Security managers struggling with allocating resources to noise and slow response times can automate the analysis, triage, remediation, and response using ASA’s auto-remediation and auto-review along with user report auto-replies.
When enabled for user reports, ASA is invoked automatically as an Automation with the trigger “User Report received” after an end-user reports a message.
When enabled for suspicious flagged messages, ASA is invoked automatically as an Automation with the trigger "Detection Rule flagged" after Attack Score returns suspicious, unknown, or error
After being invoked, ASA completes analysis and comes up with a verdict, one-liner, and executive summary for the message group.
ASA uses the same Sublime tools as an analyst, such as
- Analyzing detonated files and determining malicious content
- Perform visual analysis on logos
- Accessing sender profiles to determine prevalence and previous labels
- Identifying potential misclassification of messages and why
Getting started with ASA
To enable ASA in your environment, you just have to activate the “Send user reports to ASA” and "Send suspicious messages to ASA" Automations.
To leverage both of ASA's Automations, you must be an Enterprise customer with an abuse mailbox set.
- To get a demo of Sublime Enterprise, reach out here!
- If you’re an Enterprise user but haven’t set up your abuse mailbox yet, check out our documentation on enabling user-reported phishing on your account.
- Test out ASA in the free, public EML Analyzer by opening any sample message
Availability
ASA operates in our cloud environment (SaaS deployment) or your AWS cloud (self-hosted) at the moment. Data remains within the Sublime environment and is not shared with third parties including model providers.
The following AWS regions are currently supported:
- USA - Virginia
- USA - Oregon
- USA - Ohio
- EU - Dublin
- UK - London
- AU - Australia
To get on the waitlist for additional region support, reach out to [email protected]!
Configurations
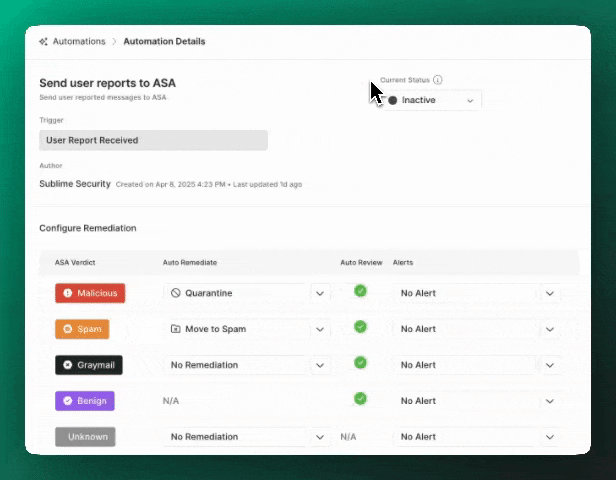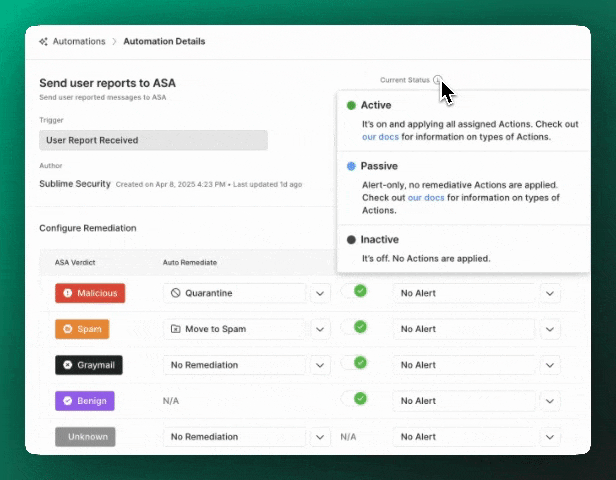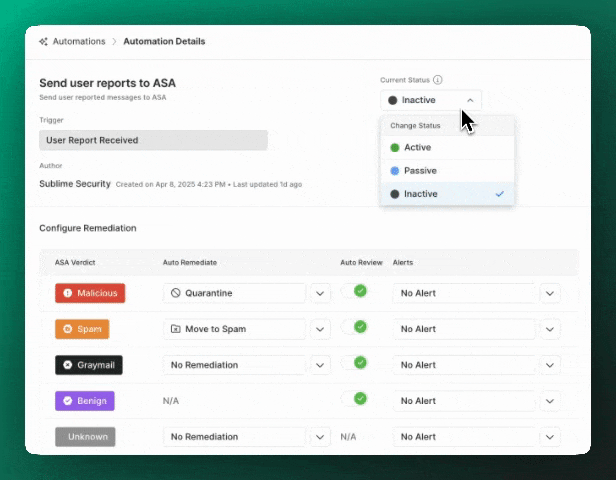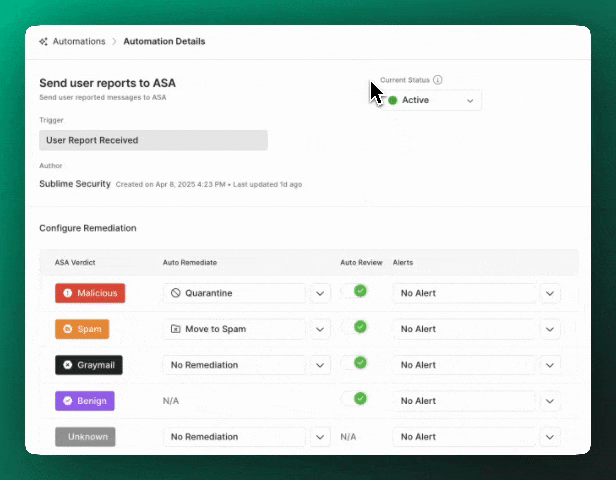
ASA defaults to inactive mode and can then be set to active or passive:
Active: “Autonomous Mode”- In its
activestate, the ASA Automation will analyze, triage, and remediate suspicious flagged or user reported messages. - You can adjust the auto-remediations, auto-review status, and custom alerts for individual ASA verdicts to give ASA as much or as little autonomy as you’d like!
- In its
Passive: “Analyst Mode”- In its
passivestate, the ASA Automation will simply analyze and alert on user reported messages. - You can set auto-remediations and auto-review status, but the Automation cannot actually apply a remediation or auto-review.
- Any custom alert Actions that are set are still applied so that you can receive alerts upon completion of the analysis.
- In its
Verdict-based auto-remediation, auto-review, and custom alert Actions
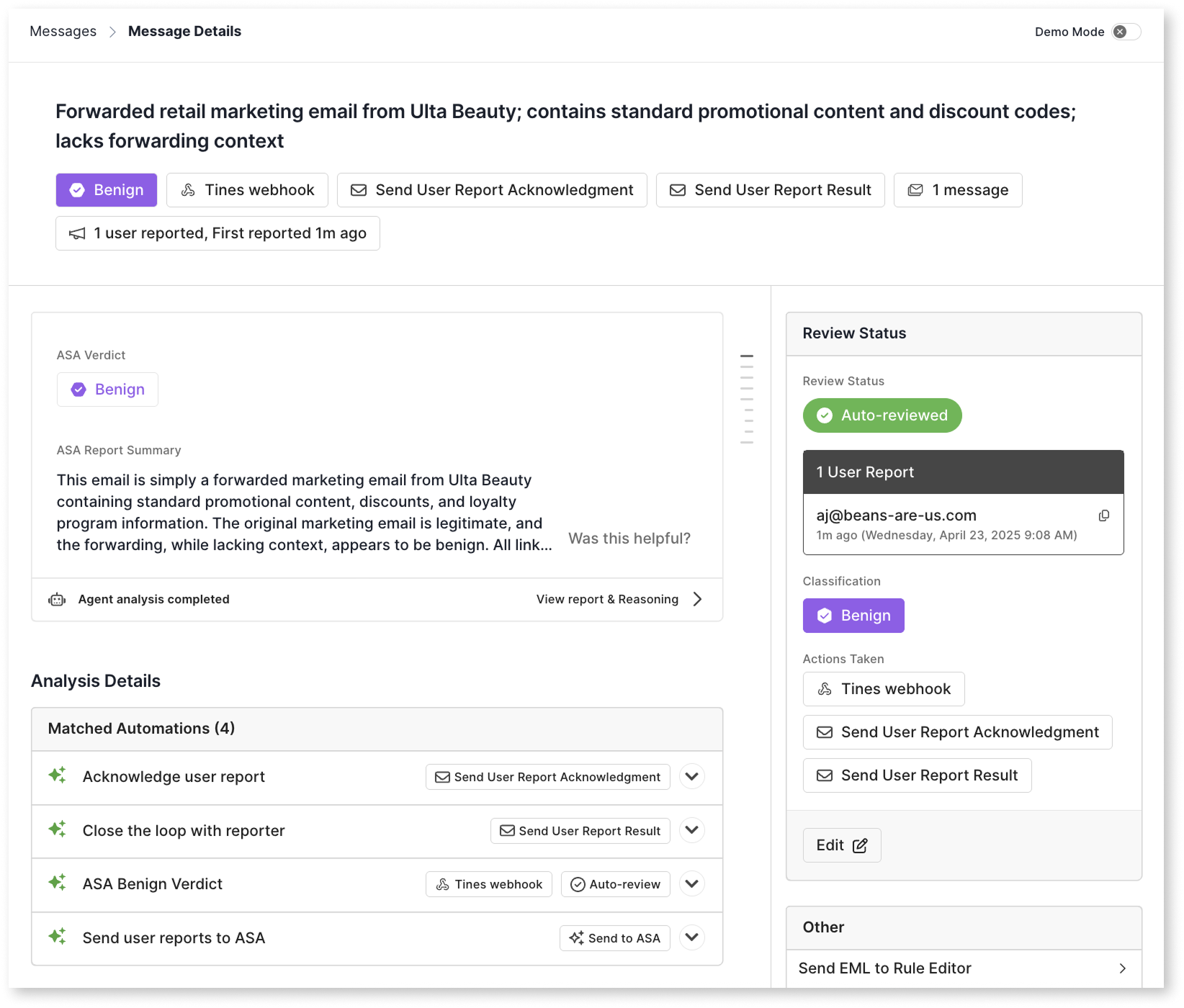
ASA classifies messages into the following verdict categories:
MaliciousSpamGraymailBenignUnknown
Outside of unknown, all of ASA’s verdicts align 1:1 with a Sublime message classification option for easy message triage and review. Unknown verdicts are rare and indicate that a message needs human review.
You’re able to select an auto-remediation approach for each of the verdicts, with an exception for benign verdicts. Options for auto-remediation include:
- Quarantine
- Trash
- Move to spam
- Add a warning banner
Auto-review is available for the malicious, spam, graymail, and benign verdicts because there’s a corresponding review classification. Auto-review is unavailable for unknown verdicts that require human review.
Custom alert Actions — webhooks, Slack alerts, and email alerts — can be applied on all ASA verdicts for easy integration with SIEM and SOAR workflows.
ASA Report
ASA provides comprehensive analysis reports for each message, presenting information in a clear, accessible format.
One-liner
A concise summary of the message’s key attributes that’s available on the message details.
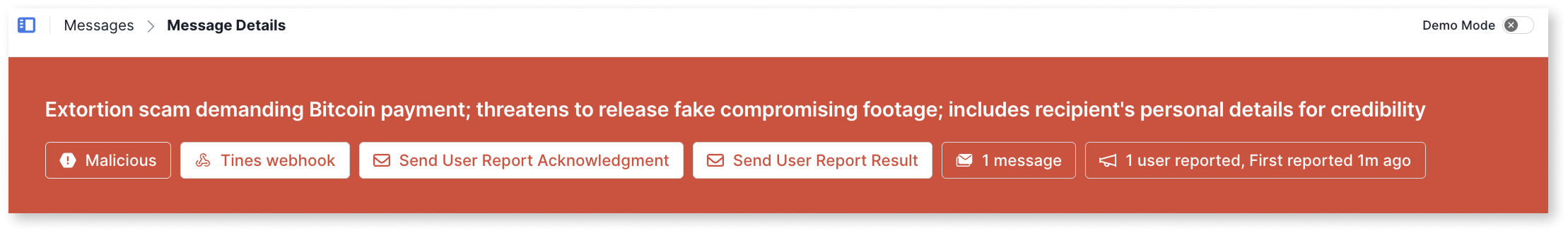
On the message details page, the one-liner also includes some message statistics:
- The ASA verdict (unreviewed messages)
- The message classification (reviewed messages)
- Actions that have been applied
- Messages count
- User report count
- First user report timing
Executive Summary
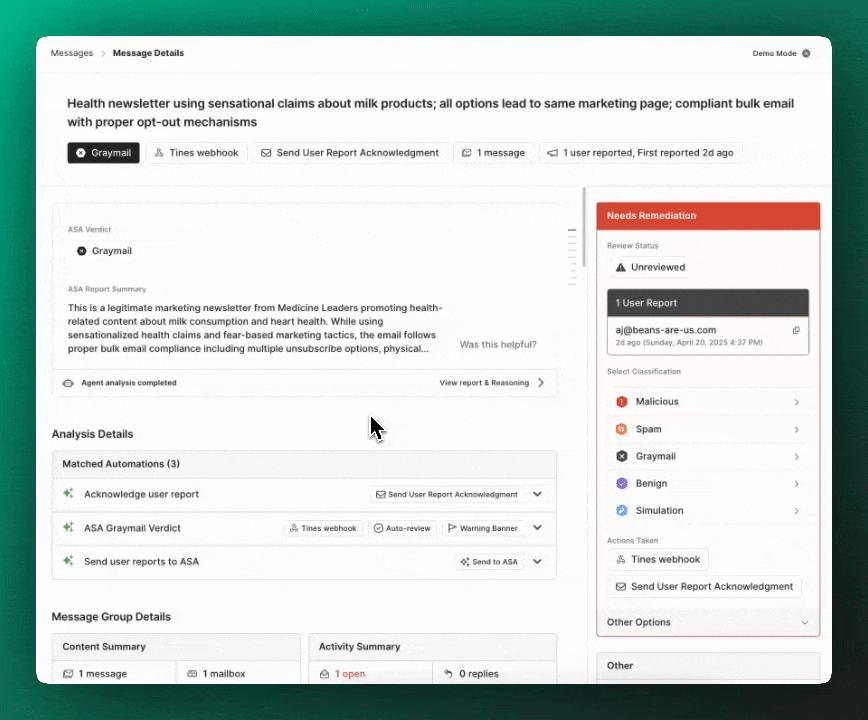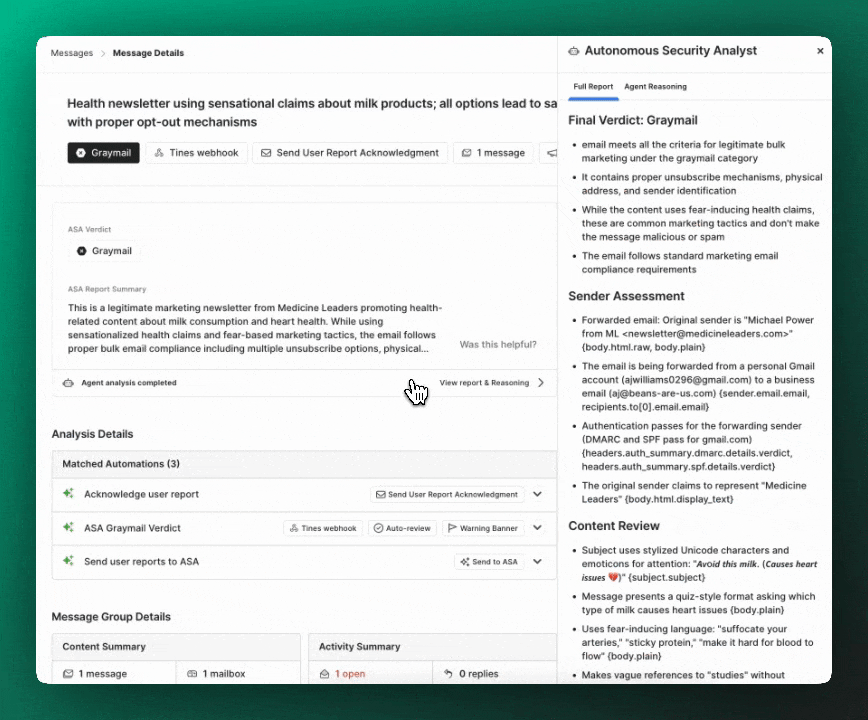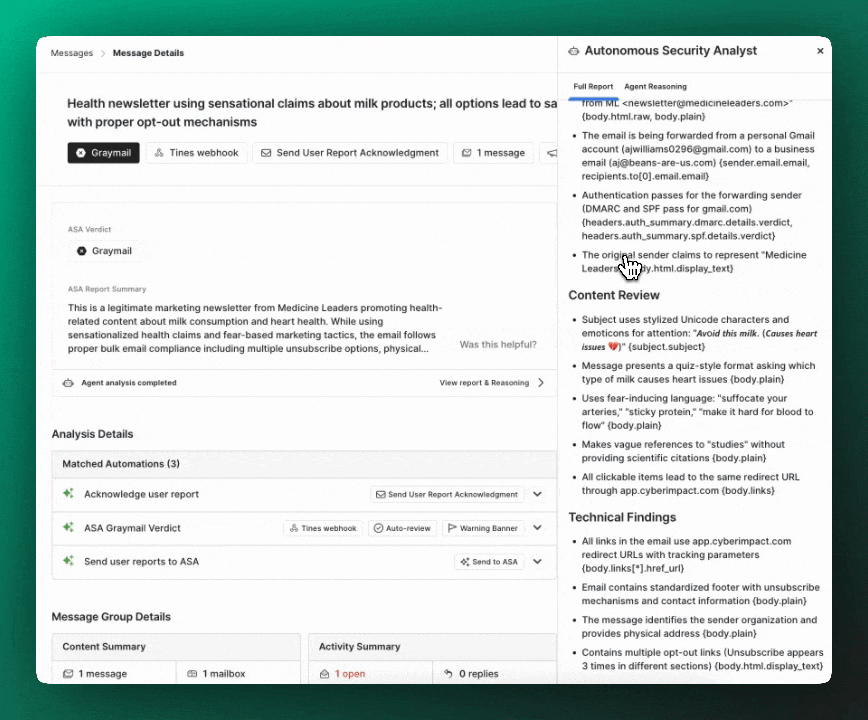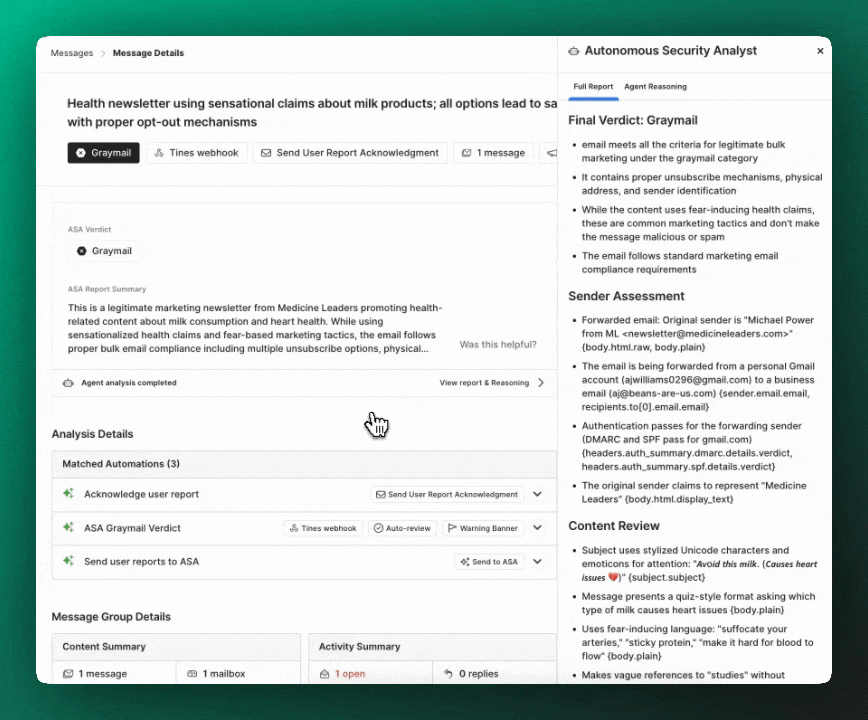
A short, detailed summary of message intent, content, links, and attachments with critical information to help analysts quickly make decisions on appropriate response to a given user report.
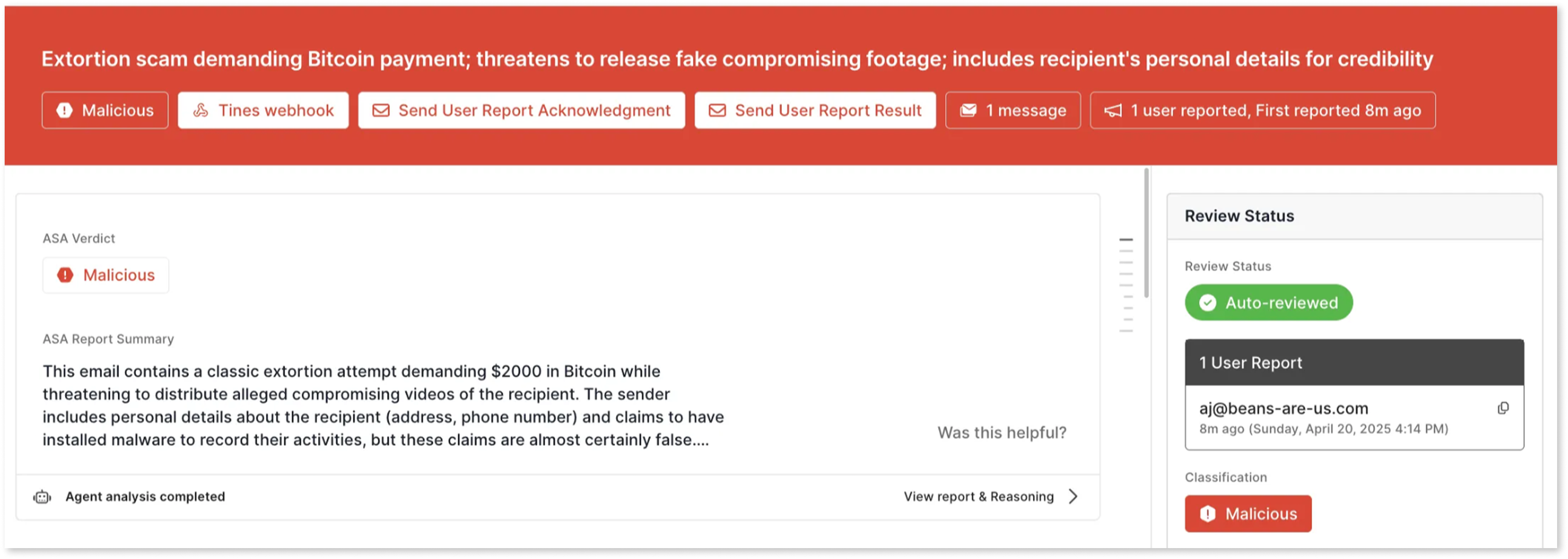
Full report and reasoning
The full ASA analysis report and agent reasoning is available for user-reported messages so that you can do in-depth investigations.
The report is a full, detailed breakdown including:
- Full attack chain analysis (for
maliciousverdicts) - Sender and content analysis
- Details from detonated files and links
- Contextual findings from sender profiles
- Explanation of signals and Detection Rules that fired (or didn't fire)
- An overall verdict explanation
Use Cases
Expedited analyst decisions with ASA analysis
In passive ”Analyst Mode”, ASA provides enhanced context to security analysts without taking automatic remediation actions.
- ASA kicks off analysis when a message is reported or Attack SCore finds it
suspicious,unknown, orerror - ASA’s analysis report is available when any analyst opens a user report (and coming soon, via API too!)
- Analysts review ASA's one-liner and executive summary to make fast, informed decisions
- Analysts check out ASA’s full report as-needed for in-depth investigations
- User report mean time to respond (MTTR) is accelerated with ASA’s contextual analysis
- Security teams maintain control over final remediation decisions and message classifications while reaping the benefits of ASA’s analysis.
Autonomous reviews with an analyst escalation path
In active ”Autonomous Mode”, ASA functions as a fully autonomous security agent with the ability to automatically remediate and review suspicious flagged message or user reports.
- ASA kicks off analysis when a message is reported and automatically remediates and classified messages based on verdict-level settings:
- Dismisses benign and graymail false positive user reports
- Quarantines malicious messages
- Trashes/junks spam and graymail messages
- Automatically classifies messages using the ASA verdict
- Escalates unknown classifications to human analysts
- Security teams only intervene when ASA determines human expertise is needed.
- The Automation works 24/7 to process the queue of user reports, even when analysts are offline.
This mode significantly reduces the workload on security teams while maintaining effective threat protection.
Updated 11 days ago