Automations
Overview
Automations are used for auto-triaging flagged and user reported messages. Automations take high confidence remediative Actions to improve analyst efficiency.
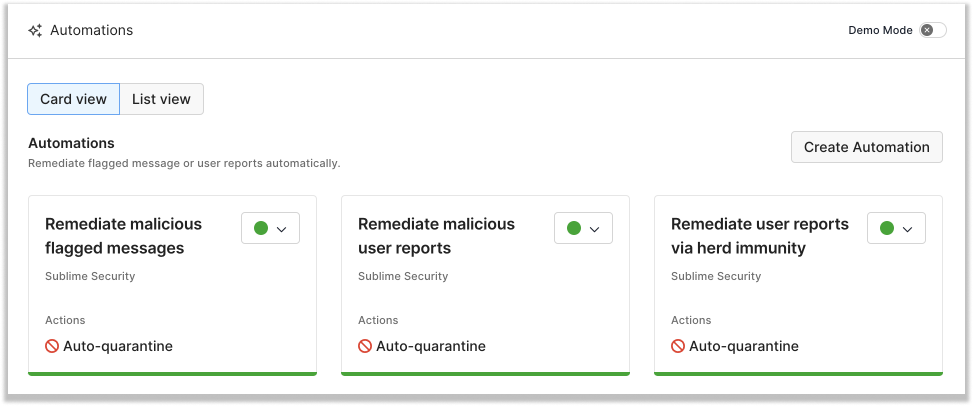
Here are a few ways organizations are using Automations today:
- Auto-quarantine flagged messages with a Malicious Attack Score verdict
- Auto-quarantine campaigns when multiple Detection Rules flag
- Auto-quarantine entire campaigns based on a number of user reports
- Trigger an email alert whenever a VIP user reports a message
- Apply a warning banner to any flagged message when the recipient is a VIP
What are Automations?
Automations are MQL logic compared against messages, just like a Detection Rule. However, Automations use triggers to designate which type of message is eligible for analysis and then apply Actions to matching messages. The trigger for an Automation is when a user reports a message and/or when any Detection Rule flags a message.
Automations also have a special active status, passive mode, that allows you to run an Automation over incoming messages and receive alert-based Actions like webhooks, but without applying remediative Actions like Auto-quarantine, Auto-trash, or Auto-banner.
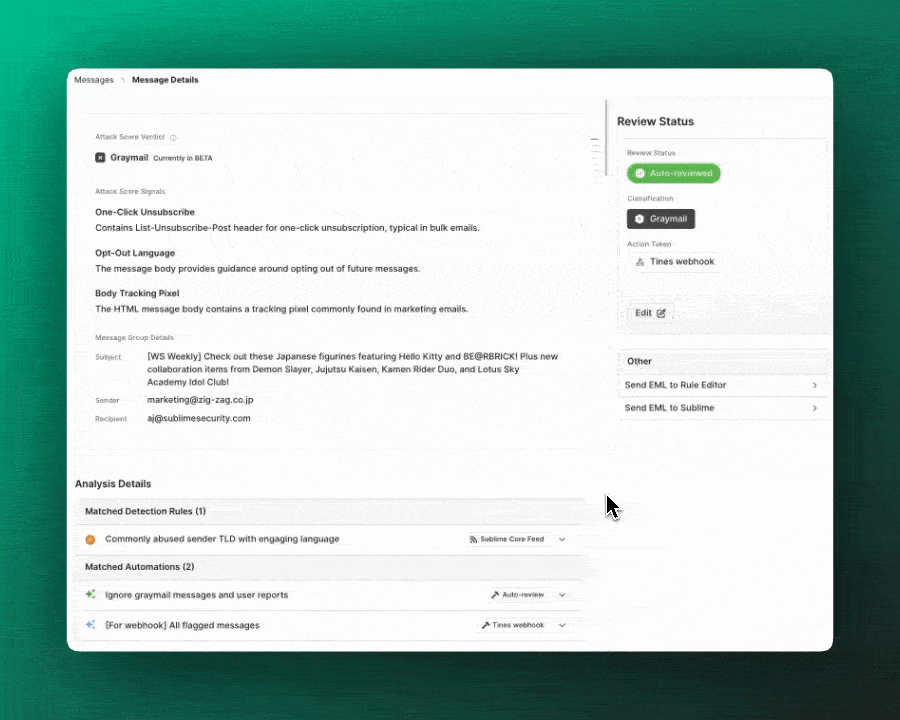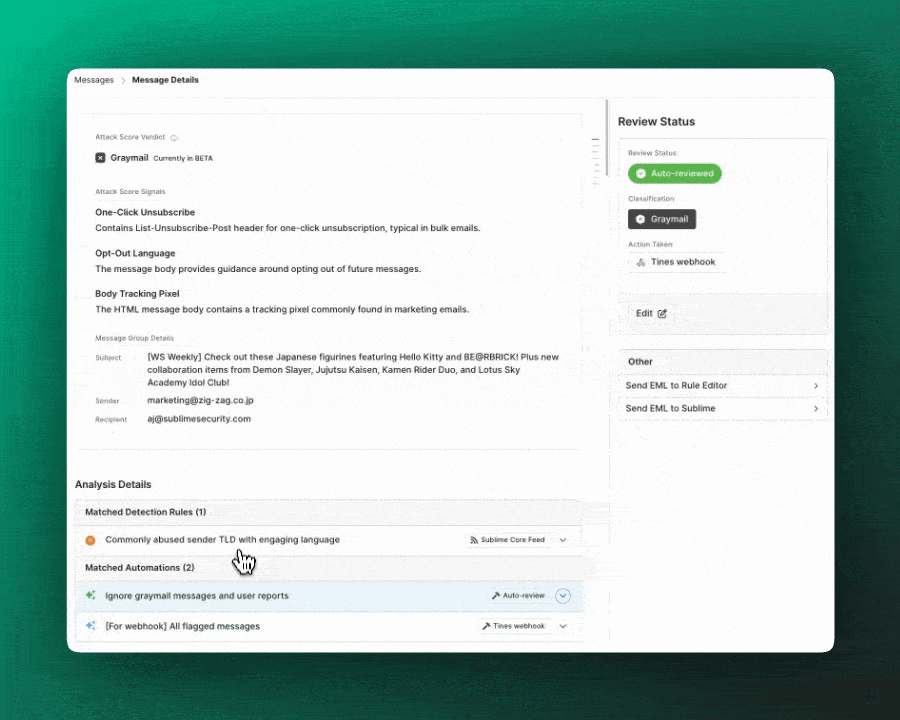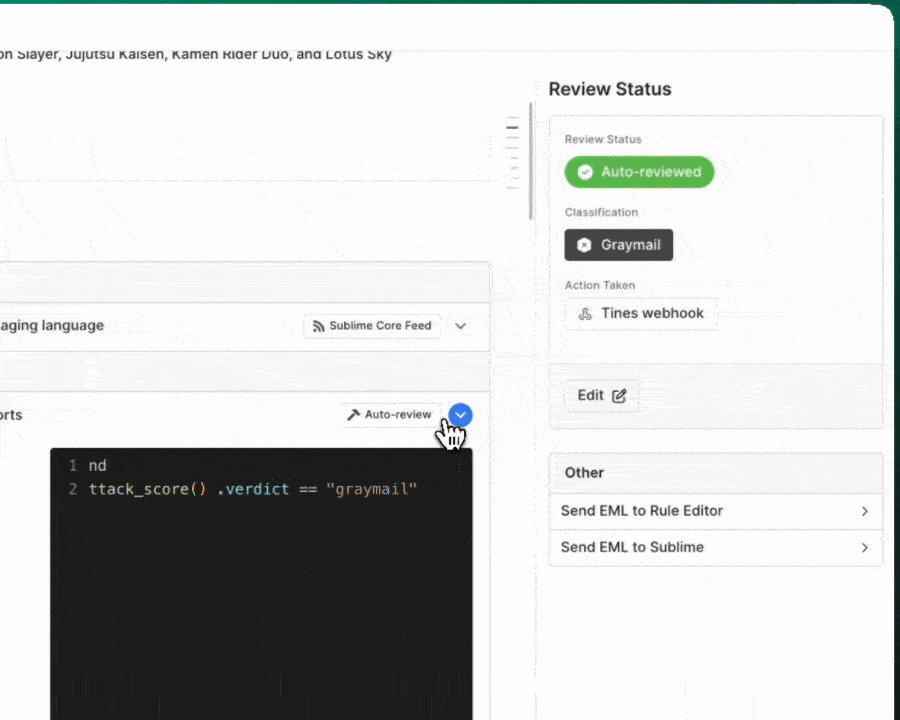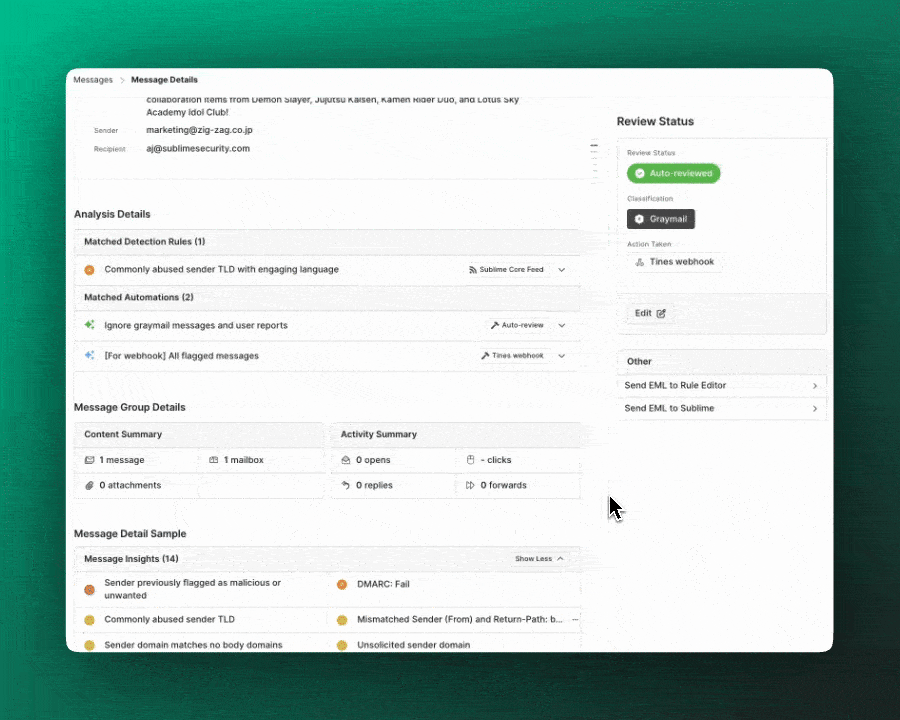
Sublime shares recommended Automations in the Core Feed, just like Detection Rules. Core Automations are inactive by default and come with default Actions, so you can easily kick off your automated response to malicious attack patterns. You can set Core Automations to active to get coverage against malicious messages or to passive mode to observe the Automations in your environment without the default Action!
When writing Automations, you may reference special functions -- beta.attack_score and triage. -- that aren't available in Detection Rules:
ml- Machine learning functions.attack_score()- Attack Score information about a given message.verdict-*string*- A description —malicious,suspicious, orunknown— to communicate the likelihood of a given message being an attack.score-*float*- A number from 0-100 calculated by the ML algorithm, with higher scores indicating a higher correlation with messages involved in attacks
triage- Message (group) information available during the evaluation of Automations:.user_reports- Aggregate information about user reports for the message group.count-*number*- A count of the number of times this message group has been reported by distinct users
.flagged_rules- List of all Detection Rules that matched any message in the group.attack_types-*array of strings*- Attack types associated with the Rule.detection_methods-*array of strings*- Detection methods associated with the Rule.name-*string*- Name of the Rule.severity-*string*- Severity level of the Rule.tactics_and_techniques-*array of strings*- Tactics and techniques associated with the Rule.tags-*array of strings*- Tags associated with the Rule, including user provided tags.feed- Information about the feed containing this rule, ornullif the rule didn't come from a feed.name-*string*- Name of the feed.is_core-*boolean*- Whether the feed is the Sublime Rules Feed
Example Automations
Flagged or user reported messages with a malicious Attack Score verdict
- Trigger: flagged message, user report
- Recommended Action: auto-quarantine, auto-review
type.inbound
and ml.attack_score() .verdict == "malicious"
Flagged or user reported messages with a suspicious Attack Score verdict
- Trigger: flagged message, user report
- Recommended Action: warning banner
type.inbound
and ml.attack_score() .verdict == "suspicious"
User reported message with more than 1 report
- Trigger: user report
- Recommended Action: warning banner
type.inbound
and triage.user_reports.count > 1
Flagged messages with more than 3 matching Detection Rules
- Trigger: flagged message
- Recommended Action: auto-quarantine
type.inbound
and length(triage.flagged_rules) > 3
Flagged messages that landed in spam
- Trigger: flagged message
- Recommended Action: auto-quarantine
type.inbound
and external.spam
Flagged or user reported messages with Detection Rules that have specific tags
- Trigger: flagged message, user report
- Recommended Action: auto-quarantine
type.inbound
and any(triage.flagged_rules, any(.tags, . == "tag name here"))
Get started
To use the user report trigger, read our docs on User-reported phishing.
To create an Automation, visit Rules > Automation and click New Automation. When you finish writing your MQL, click Create Automation. In the metadata modal, be sure to set the Triggers to “user report” and/or “flagged message”.
Updated about 2 months ago